helm-charts
🚀 Nected OnPremise Installation (via Helm Charts)
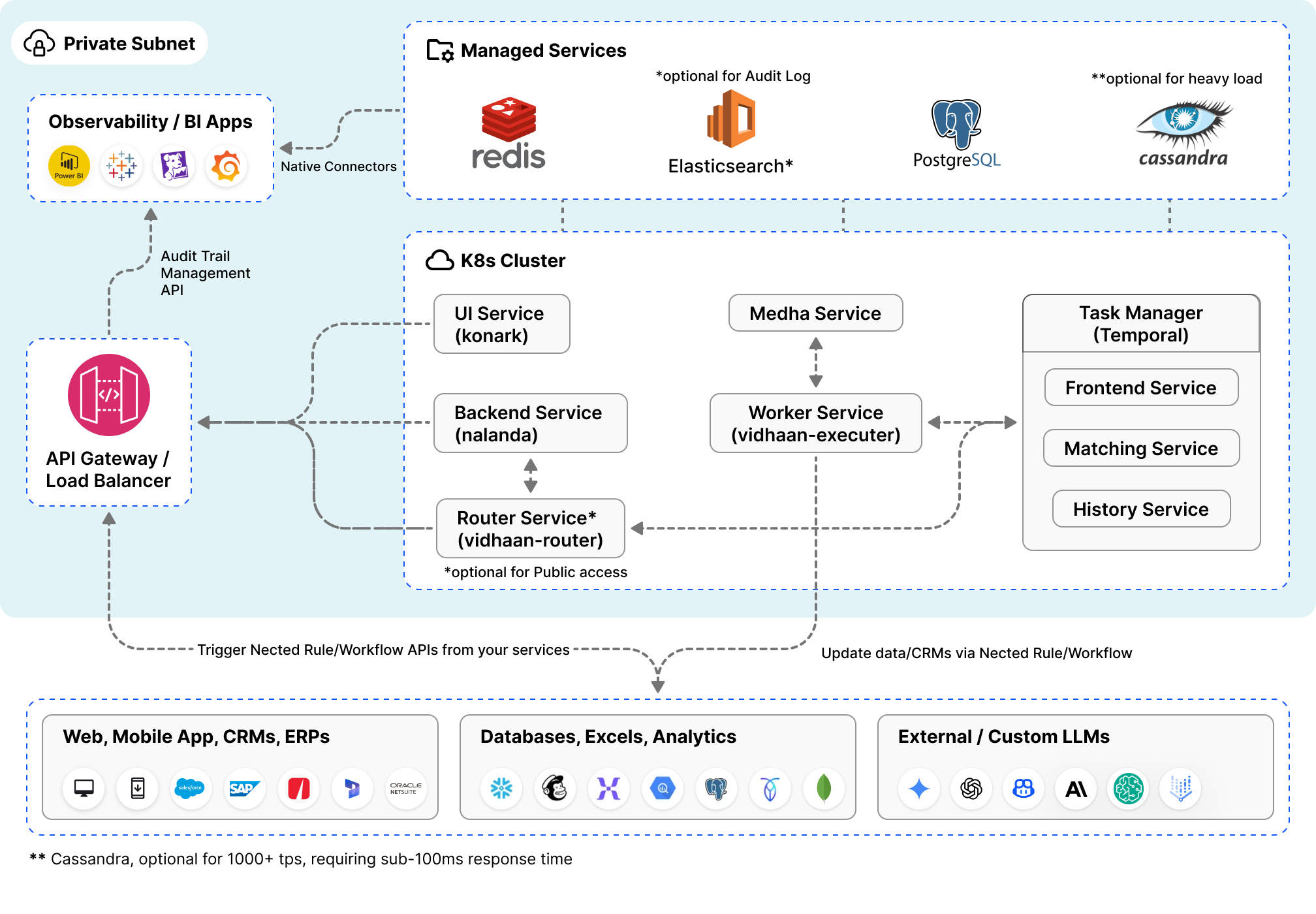
This guide walks you through deploying Nected on your own Kubernetes cluster using Helm charts.
✅ Pre-Requisites
- Application Load Balancer
- Domain Setup & Ingress Configuration
You’ll need three fully qualified domain names (FQDNs) pointing to your cluster’s ingress controller:
| Service | Values Placeholder | Example Domain |
|---|---|---|
nected-konark |
<<ui-domain>> |
app.xyz.com |
nected-nalanda |
<<backend-domain>> |
api.xyz.com |
nected-vidhaan-router |
<<router-domain>> |
router.xyz.com |
💡 Ingress Setup:
- Create
ingress.yamlfor reference download sample file.- Ingress config
- Setup ingress, once all services are deployed:
kubectl apply -f ingress.yaml
📌 Update DNS
Point each domain to your ingress controller’s external IP:
app.xyz.com→<Ingress External IP>api.xyz.com→<Ingress External IP>router.xyz.com→<Ingress External IP>
- PostgreSQL - With DB/table creation privileges
- Redis - Endpoint and credentials
- Elasticsearch / OpenSearch (Optional)
💡 For Dev Environments: Use Nected’s datastore chart if you don’t have PostgreSQL, Redis, or Elasticsearch installed:
- Datastore values
- Install chart
helm upgrade -i datastore nected/datastore -f datastore-values.yaml
🛠️ Installation Steps
📦 Add Helm Repo
helm repo add nected https://nected.github.io/helm-charts
📄 Download Sample Values Files
🌐 Configure Scheme and Domains
In nected-values.yaml, replace the following placeholders:
| Values Placeholder | Replace With |
|---|---|
<<scheme>> |
http or https |
<<ui-domain>> |
app.xyz.com |
<<backend-domain>> |
api.xyz.com |
<<router-domain>> |
router.xyz.com |
🔐 Configure default user credentials
In nected-values.yaml:
NECTED_UI_USER_NAME: &uiUserName dev@nected.ai
NECTED_UI_USER_PASSWORD: &uiUserPassword devPass123
🗄️ Configure PostgreSQL
- In
temporal-values.yaml:NECTED_PG_HOST: &pgHost datastore-postgresql NECTED_PG_USER: &pgUser nected NECTED_PG_PASSWORD: &pgPassword psqlPass123 NECTED_PG_PORT: &pgPort 5432 NECTED_PG_TLS_ENABLED: &pgTlsEnabled false NECTED_PG_HOST_VERIFICATIO: &pgHostVerification false - In
nected-values.yaml:NECTED_PG_HOST: &pgHost datastore-postgresql NECTED_PG_DATABASE: &pgDatabase nected NECTED_PG_USER: &pgUser nected NECTED_PG_PASSWORD: &pgPassword psqlPass123 NECTED_PG_PORT: &pgPort "5432" NECTED_PG_SSL_MODE: &pgSslMode disable
Azure PostgreSQL Flexible Server
- Go to the Azure Portal, Navigate to your PostgreSQL Flexible Server instance.
- Open “Server Parameters”, In the left-side menu under Settings, click “Server Parameters”.
- Find the azure.extensions parameter, Search for azure.extensions using the search bar.
- Add btree_gin to the list, If btree_gin is not already listed, append it to the existing list. Example: hstore,pg_trgm,btree_gin
- Click Save, This change will not restart the server—it takes effect immediately. Create the Extension in Your Database.
- After enabling it in parameters:
CREATE EXTENSION IF NOT EXISTS btree_gin;Notes: No changes required if using the Nected-provided datastore.
🧠 Configure Redis
In nected-values.yaml:
NECTED_REDIS_TLS_ENABLED: &redisTlsEnabled "false"
NECTED_REDIS_INSECURE_TLS: &redisInsecureTls "true"
NECTED_REDIS_HOST_PORT: &redisHostPort datastore-redis-master:6379
NECTED_REDIS_HOST: &redisHost datastore-redis-master
NECTED_REDIS_PORT: &redisPort "6379"
NECTED_REDIS_USERNAME: &redisUser ""
NECTED_REDIS_PASSWORD: &redisPassword ""
Notes: No changes required if using the Nected-provided datastore.
🔍 Configure Elasticsearch / OpenSearch
In nected-values.yaml:
NECTED_ELASTIC_ENABLED: &elasticEnabled "true"
# possible values: managed / opensearch
NECTED_ELASTIC_PROVIDER: &elasticProvider managed
NECTED_ELASTIC_HOSTS: &elasticHost http://elasticsearch-master:9200
NECTED_ELASTIC_INSECURE_TLS: &elasticInsecureTls "true"
NECTED_ELASTIC_API_KEY: &elasticAPiKey ""
NECTED_ELASTIC_USER: &elasticUser elastic
NECTED_ELASTIC_PASSWORD: &elasticPassword esPass123
Optional: To disable audit logging:
NECTED_ELASTIC_ENABLED: &elasticEnabled "false"
Notes: No changes required if using the Nected-provided datastore.
🚀 Install Nected Services
- Install Temporal:
helm upgrade -i temporal nected/temporal -f values/temporal-values.yaml - Install Nected:
helm upgrade -i nected nected/nected -f values/nected-values.yaml
✅ Access the Application
Visit the application via your configured <<ui-domain>>.
Login using default credentials defined in nected-values.yaml:
NECTED_USER_EMAIL: dev@nected.ai
NECTED_USER_PASSWORD: devPass123
🤝 Community & Support
For questions, feedback, or contributions:
- Visit our documentation
- Join the conversation on LinkedIn
- Contact the team via support@nected.ai